First, create a key: crypto key generate rsa label mykey modulus 2048 Next, create a trustpoint which references the key, and generate a self-signed certificate: crypto ca trustpoint throwaway keypair mykey enrollment self crypto ca enroll throwaway noconfirm Now the throwaway trustpoint has a certificate. Export that certificate to the terminal. That would be likely due to the missing of the rsa key pair as you doubted. Please try to issue the command crypto key generate rsa modulus 1024 and see if it works, otherwise try the following: crypto key generate rsa label NIMA modulus 1024. Ip ssh rsa keypair-name NIMA. With a given key pair, data that is encrypted with one key can only be decrypted by the other. This is useful for encrypting data between a large number of parties; only one key pair per person need exist. RSA is widely used across the internet with HTTPS. To generate a key pair, select the bit length of your key pair and click Generate key.
UPDATE: Please read my updated post regarding SSH on Cisco IOS.

On my previous blog post, I talked about one of the things a Network Engineer must do to harden Cisco routers and switches. Today, I am adding another one to the list. I will try to keep adding to this list to raise the importance of security.

As the title says, I am going to show you on how to enable SSH on Cisco IOS devices. The commands are pretty much the same in pretty much all of the IOS versions. If the commands listed here didn’t work, then use the IOS help menu.
The majority, if not all, of the people, know that Telnet sends data in clear text. That said, usernames and passwords are up for grabs. Imagine an unauthorized user logging into company’s Cisco IOS devices and deleting the configuration and rebooting them. When that happens, someone would be let go pretty soon.
To enable SSH on Cisco IOS, you need to have crypto feature in the IOS. If the IOS does not support crypto, then you’re out of luck. If you have a SMARTnet contract, I suggest you upgrade the IOS. For legacy hardware, the only choice is to upgrade it to a newer version. Please check Cisco Feature Navigator to check your IOS if it supports the crypto feature.
Enabling SSH on Cisco IOS
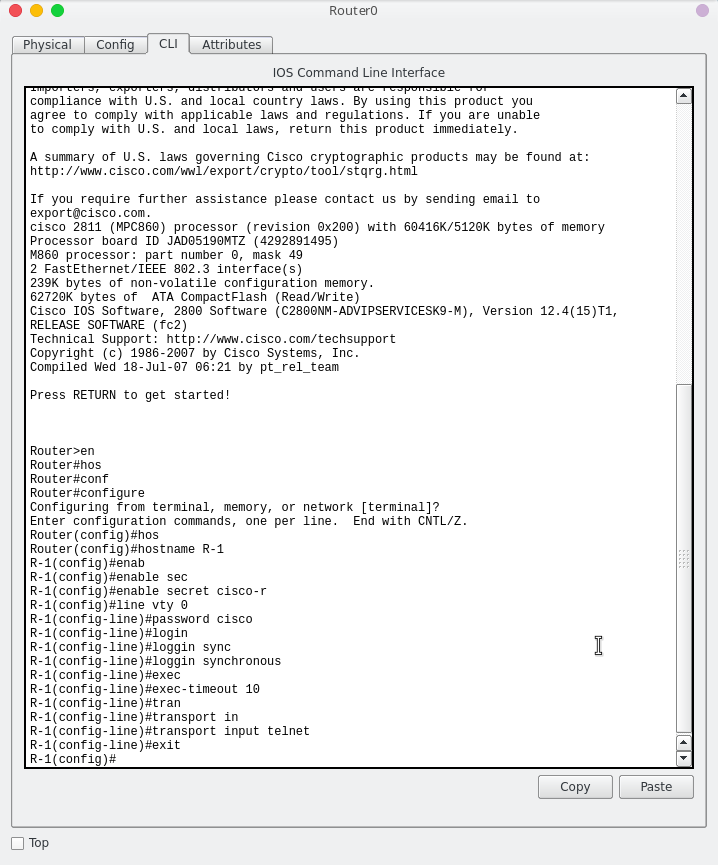
Without further delay, below are the commands to enable SSH on Cisco IOS. With this method, Cisco IOS requires the user to specify the host name and domain name.
Alternatively, Cisco IOS user could enable SSH without specifying the domain name, as shown below. In this case, I am using 4096-bit key size for the RSA keys.
While you don’t need to use the transport input ssh command, it is recommended to disable Telnet altogether. By default, line vty 0 to 15 has the command transport input all configured but not showed in the running configuration or startup configuration. That said, it will allow you to use either SSH or Telnet.
Final Words
Hopefully, this will be included in your standard configuration for all Cisco routers and switches that you have. Telnet is a considered a security risk, so enabling SSH will mitigate security risk on your network.
I hope this has been helpful and thank you for reading!
Are you ready to improve your network security?
Let us answer more questions by contacting us. We’re here to listen and provide solutions that are right for you.
You might also like to read
Want to learn more about the basics of securing Cisco networks?
Crypto Key Generate Rsa Label
Disclosure
Generate Rsa Key Pair
NetworkJutsu.com is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com.
